Что такое Мультисигнальные мошенничества и как пользователи могут защитить себя?
В темном лесу криптовалютного мира инциденты взлома продолжают появляться один за другим. По данным компании по безопасности блокчейн PeckShield, в 2024 году произошло более 300 инцидентов взлома криптовалют, что привело к общим потерям в размере 2,15 миллиарда долларов — увеличение на 30% по сравнению с 1,51 миллиарда долларов в 2023 году. Хакеры рассматривают различные сектора как свои персональные банкоматы, в частности, мошенничество, связанное с кошельками, особенно распространено, включая схемы Мультисигнал.
Мошенничество с мультисигналом - это форма мошенничества, которая манипулирует кошельками, эксплуатируя механизм мультиподписи (обычно называемый мульти-сиг), в результате чего пользователи теряют контроль над своими кошельками и крадут их активы. В то время как первоначальная цель системы мультисигнала - повышение безопасности кошелька, ее врожденная сложность часто становится точкой входа для мошенников. В этой статье мы рассмотрим механизм мультисигнала - изучим, как он работает, его плюсы и минусы, кейс-стади реального мира и в конечном итоге предоставим пользователям стратегии предотвращения для лучшей безопасности их цифровых активов.
Что такое механизм Мультисигнала?
Механизм мультиподписи (мультисиг) широко используется как техника безопасности в криптовалютной и блокчейн сфере. Для совершения транзакций или выполнения важных операций требуется совместное одобрение нескольких держателей частных ключей, что позволяет нескольким пользователям совместно управлять и контролировать доступ к одному криптовалютному кошельку. По сравнению с системами с одним ключом механизм мультиподписи предлагает значительно большую безопасность и гибкость благодаря распределенной авторизации. Он особенно подходит для сценариев, таких как совместная работа команды, управление активами институций и управление DAO.
Для того чтобы объяснить простыми словами, мультисигнальная система представляет собой высокоэффективный сейф, который требует использования нескольких ключей для открытия. Это означает, что даже если один или несколько закрытых ключей будут потеряны или скомпрометированы, активы кошелька могут остаться в безопасности.
Ключевые вехи в развитии механизмов Мультисигнала
- 2012: протокол P2SH (Pay-to-Script-Hash) Bitcoin представил возможность встраивания мультисигнальных скриптов в транзакции с помощью хеширования.
- 2016: Криптовалютная биржа Bitfinex приняла решение использовать мультисигнальное решение BitGo для управления активами пользователей. Однако из-за неправильной конфигурации в горячем кошельке было похищено 120 000 BTC.
- 2017: Кошелек Parity Multisig был атакован из-за уязвимости кода, что привело к краже приблизительно 150 000 ETH.
- 2020: Команда Gnosis официально запустила Gnosis Safe, первое стандартизированное решение для мультисигнал-кошелька в экосистеме Ethereum. В том же году EIP-3074 Ethereum предложил опкоды AUTH и AUTHCALL, которые позволяют внешне владеющим счетам (EOA) авторизовывать контракты на выполнение транзакций от их имени, обеспечивая базовую поддержку для мультисигнала.
- 2021: предложен EIP-4337 Ethereum об абстракции учетной записи через смарт-контракты, обеспечивающий более гибкое управление разрешениями для кошельков с мультисигналами.
- 2023: EIP-4337 был официально внедрен. В том же году была обнаружена уязвимость контракта в Safe (ранее Gnosis Safe). Атакующий использовал недочет в логике проверки подписи, чтобы подделать мультисигнальные транзакции и украсть средства. В ответ на это команда Safe незамедлительно устранила проблему, ввела модульную систему аудита безопасности и запустила новую функцию «отложенного исполнения».
- 2024: Предложение EIP-7702 позволило адресам EOA временно получить функциональность смарт-контракта в рамках одной транзакции, дополнительно упрощая логику мультисигнала.
Как работают Мультисигнал кошельки
В основе механизма мультиподписи лежит концепция пороговых подписей, что означает, что транзакция может быть завершена только тогда, когда достигнуто заранее определенное количество действительных подписей (порог). Это обычно выражается в формате "m из n", где m - это количество необходимых подписей, а n - общее количество задействованных частных ключей. Например, в кошельке с 2 из 3 мультиподписями установлены три частных ключа, но достаточно любых двух из них для авторизации транзакции.
Возьмем кошелек TronLink, поддерживающий Мультисигнал, в качестве примера, рабочий процесс функционирует следующим образом:
1) Управление и распределение закрытого ключа
После создания или импорта кошелька пользователь переходит в раздел «Управление разрешениями» в разделе «Управление кошельком». Мультисигнальная система разрешений TRON определяет три уровня доступа: Владелец, Свидетель и Активный, каждый из которых имеет разные функции:
- Владелец: Это самый высокий уровень полномочий в учетной записи. Он контролирует собственность, управляет структурами разрешений и может выполнять любой контракт. При создании новой учетной записи этой роли по умолчанию назначается сама учетная запись.
- Свидетель: Этот уровень доступен исключительно для супер представителей и используется для управления узлами, производящими блоки. Он недоступен для обычных пользователей. После изменения разрешений узел, производящий блоки, должен быть переконфигурирован.
- Активный: Этот уровень разрешения устанавливается и изменяется Владельцем. Он используется для выполнения конкретных задач, таких как трансферы, голосование, стейкинг, выпуск активов и создание смарт-контрактов.

Источник: TronLink
Пользователи могут изменять разрешения, добавлять адреса приватных ключей, принадлежащие различным сторонам, и настраивать пороговое значение в соответствии со своими потребностями. Количество приватных ключей должно быть равно или больше порогового значения. Например, в настройке 3 из 5 пользователь добавляет пять приватных ключей, и любые три из них должны подписать транзакцию, чтобы она была действительной.
2) Подписание и исполнение транзакции
После завершения установки пользователь A инициирует запрос на перевод, что заставляет систему создать неподписанную транзакцию. Пользователь A затем подписывает транзакцию с использованием своего закрытого ключа. После этого пользователь B, пользователь C или другие держатели ключей подписывают по очереди, пока не будет собрано необходимое количество подписей. После достижения порога транзакция проверяется и транслируется в сеть блокчейна для выполнения.
Преимущества и недостатки механизма Мультисигнал
Исходя из того, как работает механизм мультиподписи, его преимущества очевидны и убедительны:
1) Значительное повышение безопасности
- Предотвращает единичные точки отказа: когда для проведения транзакций требуется несколько подписей, компрометация одного частного ключа или сбой одного устройства не приводит к потере активов.
- Защищает от угроз со стороны сотрудников: В командной среде требование нескольких одобрений значительно снижает риск того, что один человек неправомерно присвоит средства.
- Снижает риски взлома: Злоумышленнику потребуется одновременно скомпрометировать несколько частных ключей или устройств, что сделает несанкционированный доступ намного сложнее.
2) Гибкое управление активами
- Пошаговые разрешения: Для различных сценариев можно установить различные пороги. (Например: 2 из 3 для рутины, сделок с низкой стоимостью, и 3 из 5 для переводов высокой стоимости.)
- Децентрализованный управление ключами: Пользователи могут хранить личные ключи на нескольких устройствах (таких как смартфоны, аппаратные кошельки и т. д.) или в разных физических местах, что позволяет эффективно распределять риски.
3) Улучшенная прозрачность и проверяемость
Вся информация, связанная с подписями, такая как адреса, временные метки и другое, записывается публично и может быть отслежена, что значительно облегчает аудит и ответственность после события.
Однако сложность механизма мультисигнала также вносит несколько вызовов, таких как:
1) Управление сложными ключами
Хотя пороговые подписи предлагают гибкость, они также создают высокий уровень зависимости. Пользователи должны обеспечить безопасное хранение и доступ ко всем частным ключам. Если один или несколько держателей ключей станут недоступными, может оказаться невозможным достичь необходимого порога подписи — что потенциально приведет к постоянной блокировке средств. Более того, злоумышленники могут использовать тактику социальной инженерии, манипулируя доверием людей, выдавая себя за законных источники, чтобы обмануть других подписантов и дать разрешение. Это может привести к несанкционированному доступу и краже средств.
2) Высокий барьер для пользователей
Поскольку для подписания транзакций требуется согласование между несколькими сторонами, это может вызвать задержки или ошибки, особенно в срочных ситуациях
3) Высокие затраты на цепочке
На цепочках, таких как Ethereum, мультисигнальные контракты требуют нескольких раундов проверки подписей. По сравнению с транзакциями с одной подписью, это приводит к значительно более высоким затратам на газ.
4) Риск технических уязвимостей
Мультисигнал не является абсолютно надежным. Если у системы кошелька или самого контракта есть уязвимости, хакеры могут использовать их для кражи средств.
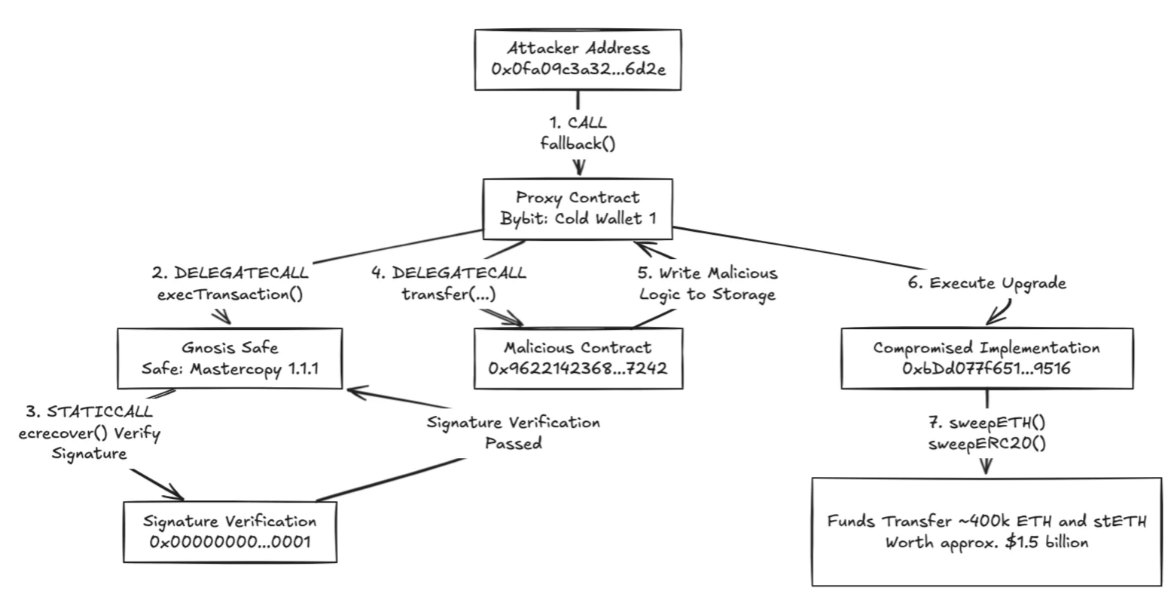
Процесс атаки Bybit (Источник: Команда безопасности SlowMist)
Например, 21 февраля 2024 года мультиподписной кошелек криптовалютной биржи Bybit был специально нацелен и скомпрометирован. Хакеры использовали функцию вызова deleGate.iocall в безопасном контракте кошелька Safe мультиподписи, внедряя зловредный контракт для переопределения правильной логики. Это позволило мошенническим транзакциям казаться легитимными на фронтенде, обманывая подписантов. В результате злоумышленник обошел процесс мультиподписной верификации и успешно перевел почти 1,5 миллиарда долларов США в активы на анонимный адрес кошелька.
Какие общие тактики используются в мошеннических схемах Мультисигнал?
По сути, мошеннические схемы с мультисигналами обычно связаны с утечками закрытого ключа или несанкционированными изменениями разрешений кошелька. Мошенники получают доступ к закрытому ключу пользователя или мнемонической фразе различными способами, а затем изменяют разрешения кошелька, добавляя свой собственный адрес в качестве совместного контролера мультисигнального счета. В таких случаях пользователи все равно могут получать средства на кошелек без проблем, но когда они пытаются вывести средства, они обнаруживают, что не могут этого сделать. Из-за этой скрытой настройки многие пользователи не понимают, что они уже потеряли контроль над своим кошельком. Мошенники часто играют в долгую игру, ждут, пока активы накопятся, прежде чем опустошить кошелек.
Итак, в каких ситуациях кошельки обычно становятся жертвами злонамеренных мультисигнальных установок?
1) Неправильное управление ключами пользователем: Некоторые пользователи сохраняют частные ключи или мнемонические фразы, делая снимки экрана, загружая их в облачные хранилища или сохраняя их на устройствах, подключенных к интернету. Хакеры могут получить их путем кибератак, и как только они получат доступ, они могут немедленно настроить злонамеренные мультисигнальные разрешения.
2) Атаки методом социальной инженерии: они поступают в различных формах. Распространенные тактики включают отправку ссылок рыболовным сайтам, ложные заявки на воздушные капли, соблазняя пользователей недорогими пополнениями, выдавая себя за техническую поддержку или членов команды, чтобы обмануть пользователей и предоставить разрешения. Эти методы могут привести пользователей к тому, что они осознанно или неосознанно раскроют закрытый ключ своего кошелька или запустят злонамеренный код умного контракта, который изменяет разрешения кошелька — в результате кошелек настроен как мультисигнал под управлением мошенника.
3) Сознательное разглашение ключа другими: В некоторых случаях мошенники притворяются, что не знают, как работать с кошельком, и предлагают свой закрытый ключ пользователю для помощи с трансфером. Однако кошелек уже настроен как мультисиг, и после того, как пользователь переводит криптовалюту в него, активы безвозвратно теряются и контролируются мошенником через разрешения мультисиг.
Как пользователи могут защитить себя?
Для полного использования преимуществ безопасности механизмов мультисигналов с минимизацией рисков пользователи должны принять двойной подход: объединение технических средств защиты с лучшими практиками поведения.
Технические меры:
- Выберите надежные услуги Мультисигнала: Приоритизируйте мультиподписные кошельки с открытым исходным кодом, прошедшие аудит безопасности со стороны третьих лиц. Оптимизируйте выбор поставщиков услуг или платформ кошельков с прочной репутацией и подтвержденной записью в области безопасности.
- Реализуйте несколько уровней безопасности: Помимо мультисигнала, пользователи также должны активировать дополнительные защитные инструменты, такие как аппаратные кошельки (например, Ledger, Trezor), двухфакторная аутентификация (2FA), антивирусное программное обеспечение и браузерные расширения, такие как Scam Sniffer, для блокировки угроз фишинга.
Поведенческие практики:
- Надежно защищайте закрытые ключи: никогда не делитесь своим закрытым ключом с кем-либо. Чтобы избежать онлайн-рисков, храните свой закрытый ключ или мнемоническую фразу офлайн, желательно записанные на прочной бумаге и надежно запечатанные в физическом месте.
- Будьте осторожны с подозрительными операциями и ссылками: никогда не нажимайте на неизвестные ссылки или не загружайте неофициальные приложения. Всегда проверяйте уведомления об аирдропах и другие коммуникации через официальные источники. Прежде чем утверждать любое взаимодействие с контрактом, внимательно изучите запрошенные разрешения — такие как утверждения токенов или обновления учетной записи — и отклоняйте все подозрительное.
- Регулярно проверяйте статус авторизации кошелька: используйте инструменты, такие как Revoke.cash, чтобы проверить и отозвать любые несанкционированные разрешения кошелька.
Навигация в мире криптовалют требует постоянного бдительности. Пользователям следует принять ум менталитет «нулевого доверия» - избегать иллюзий или фантазий о быстрой прибыли и оставаться настороже по отношению к общим ловушкам. Также важно быть информированным: узнавать о развивающихся методах мошенничества и укреплять осознание рисков.
Если пользователь обнаружит, что его кошелек злонамеренно настроен как мультисигнальный аккаунт, он должен немедленно отключиться от интернета, отключить все подключенные устройства от взаимодействия с компрометированным кошельком, отозвать разрешения через блокчейн-эксплорер и как можно скорее обратиться за помощью к профессиональной команде по безопасности.
Конечно, помимо отдельных пользователей, сам механизм мультисигнала должен продолжать развиваться, чтобы лучше защищаться от все более сложных атак. Например, интеграция MPC (многопартийных вычислений) для возможности «безключевых» подписей, позволяющая пользователям совместно подписывать транзакции, не раскрывая полных закрытых ключей; внедрение динамических защит, которые настраивают правила подписи в реальном времени на основе разведывательных данных об угрозах; и создание автоматизированных систем верификации, использующих средства искусственного интеллекта для замораживания подозрительных транзакций и запуска тревожных сигналов.
С другой стороны, регулирующие органы также начали осуществлять контроль за требованиями к соблюдению стандартов для услуг кастодиальных кошельков, включая мультисигнальные кошельки. Например, регуляция рынков криптовалютных активов (MiCA) Европейского союза, которая теперь официально вступила в силу, четко предписывает, что институты, предоставляющие услуги кастодиального обслуживания, такие как мультисигнальные кошельки, должны соответствовать требованиям по лицензированию, капиталу и отделению активов, а также соблюдать строгие стандарты операционного соблюдения.
Поскольку глобальные регуляторные рамки для управления криптовалютными активами продолжают становиться более ясными и устоявшимися, эти правила — хотя и добавляют дополнительные расходы для поставщиков услуг — в конечном итоге способствуют более прозрачной, надежной криптоэкосистеме, значительно улучшая безопасность активов пользователей.
Заключение
Механизм мультисигнала значительно улучшил безопасность и гибкость хранения криптовалюты. Избавляясь от рисков, связанных с одним частным ключом, он заложил прочный фундамент для управления активами, корпоративных приложений и инновационных финансовых услуг. Однако, как и любая сложная система, мультисигнал не защищен от эксплуатации, и мошеннические схемы, нацеленные на него, становятся все более распространенными.
Как пользователи криптовалют, важно постоянно совершенствовать осведомленность о безопасности, быть бдительными против манящих предложений и скрытых ловушек, и никогда не позволять краткосрочным выгодам привести к долгосрочным потерям. Кроме того, пользователи должны научиться умело использовать различные криптоинструменты для более эффективной защиты от потенциальных рисков.
Похожие статьи

Как вам провести собственное исследование рынка/токена (DYOR)?

Что представляет собой фундаментальный анализ?

Руководство по трейдингу для начинающих

Что такое Солана?

Риски, о которых Вы должны знать при торговле криптовалютами
